This is the multi-page printable view of this section.
Click here to print.
Return to the regular view of this page.
NetWitness Insight
Provides information about NetWitness Insight and its usage.
1 - NetWitness SaaS Offerings
Learn about the NetWitness UEBA and NetWitness Insight.
NetWitness provides two SaaS-based offerings for you to choose from based on your security needs namely NetWitness UEBA (Cloud) and NetWitness Insight. These two solutions are add-on to NetWitness® Platform.
NetWitness UEBA
NetWitness UEBA (Logs and Endpoints) takes all the traditional functions of NetWitness User Entity Behavior Analytics (UEBA) and provides them as a native SaaS application. As a cloud service, NetWitness UEBA has many additional benefits including operations from the Operations team who manage the service for your organization which enables to release new content and enhancements faster so security teams are better equipped to respond to threats.
NetWitness UEBA is an advanced analytics and machine learning solution that leverages unsupervised machine learning and empowers Security Operations Center (SOC) teams to discover, investigate, and monitor risky behaviors in their environment. All users in an organization can be analyzed for abnormal user activities using log and endpoint data already collected by your NetWitness Platform.
For existing NetWitness Platform customers, NetWitness UEBA enables analysts to:
- Detect malicious and rogue users
- Pinpoint high-risk behaviors
- Discover attacks
- Investigate emerging security threats
- Identify potential attacker’s activity
NetWitness UEBA resides on an Amazon Virtual Private Cloud (VPC) and each organization has its own VPC. If you have an on-premises NetWitness Platform deployment in your network, metadata will be uploaded to the cloud for analysis.
NetWitness UEBA performs advanced analytics on the data to enable analysts to discover potentials threats. Analysts will begin to see alerts and behavior profiles of users directly in their existing NetWitness Platform UI, and will be able to perform basic administration of the SaaS components from a dedicated SaaS UI.
For more information, see NetWitness UEBA.
NetWitness Insight
NetWitness Insight is a SaaS solution available as an extension for a NetWitness Network, Detection & Response (NDR) customer. Insight is an advanced analytics solution that leverages unsupervised machine learning to empower the response of the Security Operations Center (SOC) team. Insight continuously examines network data collected by the Decoder to discover, profile, categorize, characterize, prioritize, and track all assets actively.
NetWitness Insight passively identifies all assets in the environment and alerts analysts of their presence. The discovered assets are automatically categorized into groups of similar servers and prioritized based on their network profiles. These assets are presented to analysts to guide them to focus on certain assets to protect their organization.
Insight enables you to do the following:
- Asset discovery and characterization.
- Monitor critical Assets.
- Leverage the security operations team to triage based on prioritization.
For more information, see NetWitness Insight.
2 - Getting Started
Provides information on how to use NetWitness Insight, the first point of interaction with NetWitness Insight services.
2.1 - Welcome to NetWitness Insight
Provides an overview about NetWitness Insight.
NetWitness Insight is a SaaS solution available as an extension for a NetWitness Network, Detection & Response (NDR) customer. NetWitness Insight is an advanced analytics solution that leverages unsupervised machine learning to empower the response of the Security Operations Center (SOC) team. NetWitness Insight continuously examines network data collected by the Decoder to discover, profile, categorize, characterize, prioritize, and track all assets actively.
NetWitness Insight passively identifies all assets in the environment and alerts analysts of their presence. The discovered assets are automatically categorized into groups of similar servers and prioritized based on their network profiles. These assets are presented to analysts to guide them to focus on certain assets to protect their organization.
NetWitness Insight enables you to do the following:
- Asset discovery and characterization.
- Monitor critical Assets.
- Leverage the security operations team to triage based on prioritization.
See also
2.2 - NetWitness Insight Use Cases
Provides information about NetWitness Insight use cases.
NetWitness Insight provides advanced analytics capabilities to alert organizations about risky and anomalous assets.
Analysts must scan through billions of network sessions and IP addresses to protect their organization, searching for threats and anomalies. This is where NetWitness Insight passively identifies the assets in the enterprise to alert analysts of their presence. The discovered assets are automatically categorized into groups of similar servers and prioritized based on their network profiles. These assets are presented to analysts to guide them to focus on specific assets to protect their organization.
Use Cases
The following are typical use cases for NetWitness Insight:
- Provides asset discovery and characterization.
- Provides asset exposure rank.
- Provides efficiency in security operations through triage based on prioritization.
See also
2.3 - NetWitness Insight Architecture
Provides information about NetWitness Insight architecture.
NetWitness Insight enables analysts to get complete visibility into unknown assets and can help increase the visibility of the assets within the organization.
NetWitness Insight uses custom machine learning to process the data. The Insight Sensor collects the network metadata from the Packet Decoder and transfers metadata to the NetWitness Cloud every hour. The NetWitness Cloud merges all the network metadata received from different Insight sensors in a customer environment and provides a unified view of their network to the analysts for analysis in the Springboard assets panel view.
The Springboard assets panel queries the Cloud Connector Sensor for asset data. Cloud Connector Sensor retrieves asset data from the NetWitness Cloud and transfers it to Springboard. This helps analysts to drill down the assets data for further investigation and take immediate action.
NetWitness Insight uses unsupervised learning techniques applied to traffic associated with the assets to determine the type and significance of the asset. The services, clients, and external clients are the parameters aggregated to determine the total traffic of an asset. NetWitness Insight also computes custom importance ranks reflecting asset exposure and activity ranks so that security teams can use them to prioritize and triage incidents.
See also
2.4 - About NetWitness Insight licenses
Provides information about NetWitness Insight licenses.
NetWitness Insight licenses are valid for the time period associated with the license purchase. NetWitness Insight provides a customer-focused licensing strategy and available for NDR customers.
The following pricing is annual and can be billed monthly:
| Product |
Unit |
| NetWitness Insight (SaaS only) |
Analytics for up to 5 million IPs per day |
For additional licenses, contact NetWitness Customer Support.
See also
Log in to your NetWitness Cloud Portal
2.5 - Log in to the NetWitness Cloud Portal
Provides information on how to access NetWitness Cloud Portal
The NetWitness Cloud Portal provides administrators with the capability to manage and monitor Insight services for their account.
Prerequisites
Before you log on to the NetWitness Cloud Portal, ensure that you have received an email from NetWitness containing the account URL link.
To Log in to NetWitness Cloud Portal
-
Click on the URL provided in the NetWitness Cloud Portal welcome email.
The NetWitness Cloud Portal home page is displayed.
-
Enter your registered email ID and the temporary password in the respective fields. As this is your first login, the page prompts you to reset your password.
-
Enter the new password, and confirm the same. Review the password format rules and ensure that your new password conforms to the indicated format rules
-
Click Sign In.
See also
2.6 - Change NetWitness Cloud Portal Account Password for Insight
Provides information on changing NetWitness Cloud Portal account password for Insight.
Your NetWitness Cloud Portal account password is used for identification and authentication.
You can change your NetWitness Cloud Portal account password at any time. The password is valid for 90 days. Once the password is expired, you need to change your password. You can get an authentication code using your registered email address or your registered phone number.
If you have received a notification that your NetWitness Cloud Portal account password is about to expire, you must change your password.
Make sure that you enable Multi-Factor Authentication (MFA). To enable MFA, go to your Profile, and under Account Password, turn on Multi-Factor Authentication.
To change or reset your NetWitness Cloud Portal Account Password
-
In the NetWitness Cloud Portal login window, click Reset Password.
The Reset Password window is displayed.
-
Type the reset code that you received on your registered email address or phone number.
-
Type your new password.
-
Type your new password again to confirm.
-
Click Save.
See also
Log in to the NetWitness Cloud Portal
2.7 - Check System Status
Provides information about how to know the Insight operational health status.
Users can check the operational health status or service availability of NetWitness Insight. The operational health status indicates if all the services and integrations are operational or experiencing any disruptions. The service disruptions may be caused by server maintenance activity, regional network outages, or cloud vendor outages. These service disruptions are recorded as Incidents and displayed on Statuspage.
Users can also subscribe to receive email or Slack notifications whenever an incident occurs.
To Check the Health Status of NetWitness Insight
-
Login to NetWitness Cloud Portal.
-
Click  (View System Status). The System Status tiles are displayed.
(View System Status). The System Status tiles are displayed.
- Sensors Status: Displays the connected or disconnected sensor count.
- Operational Health: Displays the operational health details for NetWitness Insight. Status is indicated as below:
| Color |
Status |
| Green |
Indicates that NetWitness Insight is operational |
| Yellow |
Indicates that Statuspage service is unavailable |
| Red |
Indicates that NetWitness Insight is experiencing service disruptionsin the region it is deployed |
- If you observe that some services and/or integrations of NetWitness Insight are non-operational or experiencing service disruptions, click on the Operational health status tile or visit
NetWitness Statuspage and learn more about service disruptions on Statuspage.
Users can see the uptime of the past 90 days and the Incidents list on Statuspage. If there is any recorded incident on a particular day, the status bar is displayed in red color. Click View historical uptime to see the service’s historical uptime beyond 90 days.
Subscribe to System Status Update
Users can subscribe to receive email or Slack notifications whenever NetWitness SaaS Operations team creates, updates, or resolves an Incident for NetWitness Insight.
To Subscribe to the System Status Updates
-
Click on the Subscribe to Updates on the NetWitness Statuspage.
NoteUsers will receive operational status notifications for all NetWitness Cloud Services upon subscription, regardless of licensed usage.
-
If you want to receive system status updates over an email, click  .
.
Enter the email address on which you want to receive notifications and click Subscribe via Email.
-
If you want to receive system status updates over Slack, click  .
.
Click Subscribe via Slack. You will be redirected to Sign in to your workspace slack page. Follow the online instructions and provide the required details to complete the sign-in and subscription process.
See also
Install Insight Sensor
2.8 - Setup and Manage Insight Administrators
Provides information on how to set up and manage Insight administrators.
Once the tenant administrative user of an organization is onboarded into NetWitness Cloud Portal, the administrative user can perform the following tasks:
- Manage other administrative users - add, delete, enable and disable administrators, and update the profiles.
- Install, configure, and manage sensors.
- Configure and manage multi-factor authentication (MFA) for administrators.
- Temporarily enable or disable access to other administrators, instead of deleting them permanently.
Use the following table as a guide to the user management tasks that you can perform.
User Management Tasks in NetWitness Cloud Portal
Add Additional Administrators
To add an administrative user
-
Go to  Admin > Users Management > Users.
Admin > Users Management > Users.
The Users and Roles page is displayed.
-
Click Add User.
The Add User window is displayed.
-
Enter your first name, last name, email ID, and mobile number in the respective fields.
-
Click Add.
Edit User Account Settings
As an administrator, you can update the user account settings for the administrators who are configured in the system. You must ensure that the contact information of administrative users is specified so that the user receives notifications on this contact number.
To edit the administrator account settings
-
Go to  Admin > Users Management > Users.
Admin > Users Management > Users.
The Users and Roles page is displayed.
-
Select the user, and click Edit Details.
The Edit Details page is displayed.
-
Edit the first name, last name, and mobile number of the user in the respective fields.
-
Click Save.
If you are logged in and you want to edit your contact information, update your user profile by going to
User Account > Profile.
Remove an Administrator
As an administrator, you can remove the account details and access privileges for other administrators.
To delete an administrator
-
Go to  Admin > Users Management > Users.
Admin > Users Management > Users.
The Users page is displayed.
-
Click Delete User.
Enable or Disable Access for Users
You can enable or disable access for users. When you disable access for a specific user, the user cannot access the NetWitness Cloud Portal account.
If a user is logged in to NetWitness Cloud Portal and the user access is disabled, the user can continue to access NetWitness Cloud Portal until the session times out.
To enable access for a user
- Log in to the NetWitness Cloud Portal.
- Go to
 Admin > Users Management > Users.
Admin > Users Management > Users.
- Under the Users tab, select a user and click Enable User.
- To confirm, click Enable.
To disable access for a user
- Log in to the NetWitness Cloud Portal.
- Go to
 Admin > Users Management > Users.
Admin > Users Management > Users.
- Under the Users tab, select a user and click Disable User.
- To confirm, click Disable.
See also
Enable Multi-factor Authentication for Insight
2.9 - Enable Multi-factor Authentication for Insight
Provides information on how to Enable Multi-factor Authentication for Insight.
NetWitness offers Multi-factor authentication (MFA), using which you can configure an additional layer of credentials to secure your identity and manage access. If you enable MFA, then the administrative user will be prompted to additional identifications at the time of log in, such as verification code sent to the mobile number or mobile authentication application.
To Configure MFA
- Go to
 Admin > Account Settings > Multi-Factor Authentication.
The Multi-Factor Authentication page is displayed.
Admin > Account Settings > Multi-Factor Authentication.
The Multi-Factor Authentication page is displayed.
- Select ON, OFF or OPTIONAL as per your requirement.
The following table provides information on the different MFA settings that NetWitness Cloud Portal offers:
Multi-Factor Authentication Settings
| MFA Setting |
Description |
| ON |
Select ON to activate MFA. A secret code will be sent to the registered email account of the new administrators. Administrators can log in to their account, and choose between the secret code or an authentication mobile application as their preferred authentication method. |
| OFF |
Select OFF to deactivate MFA. Administrators can log in to their account with their registered email ID and password. |
| OPTIONAL |
Select OPTIONAL if you want to let the administrators decide if they want to activate or deactivate MFA for their accounts. |
See also
Setup and Manage Insight Administrators
2.10 - Configure Email Notification Preferences for Insight
Provides information on how to configure Email Notification preferences for Insight.
NetWitness Cloud Portal introduces the Email Notifications setting option that allows administrators to manage email notification preferences for Sensor Status, and License Usage. Using this setting, administrators can choose to turn on or turn off email notifications as needed, giving them more control and flexibility in managing notifications.
Note
- By default, the email notifications for License Usage are enabled, and email is sent to the users registered to the NetWitness Cloud Portal.
- By default, the email notifications for Sensor Status are disabled, and emails related to sensor status are not sent to the users. However, you can enable these notifications anytime to start receiving them.
ImportantEnabling or disabling email notifications only affects the logged-in user, as it is not a global setting.
To Adjust the Email Notification Preferences
-
Log in to the NetWitness Cloud Portal.
-
Click on your name or avatar located in the top-right corner, then click Profile (example@netwitness.com).
-
On the left side bar, click Email Notifications.
The Email Notifications page is displayed.
-
To enable a notification email, turn the toggle on ( ).
).
-
To disable a notification email, turn the toggle off ( )
)
Configure email notification preferences within the NetWitness Cloud Portal for the following event:
| Notification Type |
Description |
| Sensor Status |
This setting allows administrators to receive email notifications when the status of each sensor changes under the Sensor List tab. For example, if a sensor gets disconnected, you will receive an email notification. |
| License Usage |
This setting allows administrators to receive email notifications when their data ingestion exceeds the daily limit based on the configured license. |
See also
Enable Multi-factor Authentication for Insight
2.11 - Planning Requirements
Provides information about system requirements and various prerequisites.
Before you install the sensors, you must plan for the following:
-
The NetWitness Platform (Admin Server and Packet Decoder Host) is on version 12.3 or later.
-
Customers must have NetWitness Cloud tenant account with entitlements that allow NetWitness Insight capability.
-
Ensure you have the administrator access to the NetWitness Cloud Portal.
-
The host on which the Insight Sensor and Cloud Connector Sensor will be installed needs to be connected to Amazon Web Services(AWS). This might require changes to your existing firewall rules. Hosts will need to connect to the IP ranges for the chosen deployment region. For more information on the current list of AWS IPs by region, see
AWS IP address ranges.
-
If a proxy is identified as either the source or destination of network connections, it can limit the effectiveness of NetWitness Insight, whether it’s North-South (outbound) or East-West (lateral) traffic.
-
When a proxy is used as the source of a connection, all internal assets will appear to have the same IP addresses, as all connections are considered to originate from the same source. This can make it difficult to track the true source of connections and obtain accurate ranks, types, and categorizations.
-
When a proxy is used as the destination of a connection, all the connections will appear to be going toward the same destination. This can also cause difficulties in obtaining accurate ranks, types, and categorizations.
-
To classify assets effectively, you must decrypt the network traffic. Encrypted traffic is captured as an SSL category and hence, Insight does not have complete visibility in the data.
-
For organizations that do not follow RFC 1918 for private IP addresses, you must configure the Traffic Flow LUA parser to tag the Decoder traffic correctly. For more information on configuration, see the topic
Traffic Flow LUA Parser.
-
Ensure that the analysts have write (manage) access to create the Springboard panel. For more information, see the Springboard section in the
Role Permissions topic in the System Security and User Management Guide.
-
Ensure that the system clock is accurate. To fix the system clock, configure the NTP server on the Admin server. For more information on how to configure NTP server, see
Configure NTP Servers.
Important
- From version 12.4 or later, NetWitness no longer supports CentOS 7 and only supports Alma OS. For the Insight and Cloud Connector Sensors to upgrade to version 12.4 from lower versions, all NetWitness Platform services must be upgraded to version 12.4. This step ensures a successful upgrade for the sensors. For more information on upgrade, see NetWitness Upgrade Guide 12.4.
- For users onboarded on version 12.4, you must follow the installation procedures to deploy the sensors. For more information, see topics Install Insight Sensor and Install the Cloud Connector Sensor.
ImportantWhile performing the failover on Admin Server, if the Cloud Connector Server is found inactive. In this scenario, you must uninstall the Cloud Connector Service by running the script /var/lib/netwitness/cloud-connector-server/nwtools/uninstall-cloud-connector.sh from the Admin Server backend (NOTE: If you still see the Cloud Connector Service in the UI after running the uninstall script, restart jetty service). Once the service is successfully uninstalled, reinstall the Cloud Connector Sensor from UI to work correctly. For more information on installation, see Install the Cloud Connector Sensor.
You can install Insight Sensor on the following hosts:
| Model |
Category |
| S5/S6/S6E/Virtual |
Packet Decoder
Packet Hybrid |
NetWitness has tested and qualified the Packet Hybrid and Packet Decoders for NetWitness Insight:
The following table represents the qualified capture rate for Packet Hybrid and Packet Decoder.
| Host Type |
Qualified Capture Rate in Gbps |
| Packet Hybrid |
up to 1.5 |
| Packet Decoder |
up to 6* |
See also
3 - Install and Setup
Provides information for installing and configuring the sensors. It also provides information about deleting sensors.
3.1 - Install Insight Sensor
Provides information about how to install Insight Sensor on Packet Decoder.
You must install the Insight sensor on every Packet Decoder host to capture the network metadata and transfer them to the NetWitness Cloud. If you have multiple hosts, you need to install and configure the Insight sensor on every Packet Decoder host.
Supported Hosts
- Packet Decoder
- Packet Hybrid
Prerequisities
- Ensure that the NetWitness Platform and the host (Packet Decoder) are on version 12.3 or later.
- Ensure to consider proxy and decryption requirements when setting up an Insight Sensor. For more information, see Planning Requirements.
NoteYou need a separate Insight Sensor to be installed for each Packet Decoder host.
Step 1. Install the Insight Sensor on Packet Decoder
Step 2. Download the Activation Package
Step 3. Register the Insight Sensor
Step 1: Install the Insight Sensor on Packet Decoder
-
Log in to the NetWitness Platform as an administrator and go to  Admin > Hosts.
Admin > Hosts.
The Hosts view is displayed.
-
Select the Packet Hybrid and click  .
.
A dialog listing all the services already installed on this host is displayed and seeks your confirmation if you want to install a new service.
-
Click Yes.
The Install Services dialog is displayed.
-
Select NetWitness Insight from the Category drop-down menu, and click Install.
-
Go to  Admin > Services to verify successful Insight installation.
Admin > Services to verify successful Insight installation.
Step 2: Download the Activation Package
The activation package contains the credentials and configurations for the Insight sensor to register with NetWitness.
-
Log in to the NetWitness Cloud Portal.
-
Go to  Admin > Sensors > Downloads.
Admin > Sensors > Downloads.
-
Click the Insight tab.
-
Under Activation Package, click  to download the activation package.
to download the activation package.
Step 3: Register the Insight Sensor
Note
- The same activation package can be used to register multiple sensors.
- Ensure you use the most recently downloaded activation package.
- If the activation package is not available, generate a new one.
- The activation package contains sensitive information, you must handle it carefully and don’t share it with anyone.
- SSH to the Packet Decoder Host.
- Copy the
device-activation-package.json file downloaded from the NetWitness Cloud Portal to the /etc/netwitness/ng directory on the Packet Decoder host.
- Navigate to the following directory by running the command:
- Change the user and group of the
device-activation-package.json file to netwitness by executing the following command:
chown netwitness:netwitness device-activation-package.json
- To verify if the Insight Sensor is installed successfully, log in to the NetWitness Cloud Portal, and go to Sensor List and check if the sensor type appears as Insight with status Connected.
ImportantThere could be 10 minutes delay before the sensor status is updated correctly. For example, Registered to Connected or Connected to Disconnected.
-
Log in to the NetWitness Platform.
-
Navigate to  Admin > Services view.
Admin > Services view.
-
In the Services list, select the decoder containing the NetWitness Insight service and then click  > View > System and check if the decoder is capturing the data:
> View > System and check if the decoder is capturing the data:
- If the decoder is not capturing data, you must start data capture if you want data collected by this decoder to be part of Insight.
-
Navigate to the Explore view of the decoder containing the NetWitness Insight service. In the left panel, click cloud > config, set the parameter Aggregate Hours (aggregate.hours) from 0 to 24, and restart the NetWitness Insight service.
This step ensures that only the latest network traffic from the past 24 hours is uploaded to NetWitness Cloud, avoiding unnecessary analytics processing delays.
Important
- Asset information is collected throughout the day and uploaded every hour.
- NetWitness recommends that you do not change the configuration for daily data upload intervals. Changing this setting can affect the performance of your system.
See also
3.2 - Install the Cloud Connector Sensor
Provides information about how to install the Cloud Connector Sensor.
Cloud Connector Sensor is a new on-premises service that is installed on the Admin Server and registers as a sensor that provides a gateway to fetch the data from the NetWitness Cloud and transfer the data to the on-premises NetWitness Platform for further analysis and investigation.
Prerequisites
Ensure that the NetWitness Platform and the host (Admin Server) are on version 12.3 or later.
NoteEvery customer needs to install only one Cloud Connector Sensor in their environment.
Step 1. Install the Cloud Connector Sensor
Step 2. Download the Activation Package
Step 3. Register the Sensor
Step 1: Install the Cloud Connector Sensor
-
Log in to the NetWitness Platform as an administrator and go to  Admin > Hosts.
Admin > Hosts.
The Hosts view is displayed.
-
Select the host (Admin Server) and click  .
.
A dialog listing all the services already installed on this host is displayed and seeks your confirmation if you want to install a new service.
-
Click Yes.
The Install Services dialog is displayed.
-
Select the Cloud Connector Service from the Category drop-down menu, and click Install.
-
Go to  Admin > Services to verify successful Cloud Connector Service installation.
Admin > Services to verify successful Cloud Connector Service installation.
Step 2: Download the Activation package
The activation package contains the credentials and configurations for the Cloud Connector sensor to register with NetWitness.
-
Log in to the NetWitness Cloud Portal.
-
Go to  Admin > Sensors > Sensor Downloads.
Admin > Sensors > Sensor Downloads.
-
Click the Cloud Connector tab.
-
Under Activation Package, click  to download the activation package.
to download the activation package.
Step 3: Register the Sensor
You need to copy the Activation Package to the Cloud Connector sensor directory to complete the registration of the sensor.
Note
- The same activation package can be used to register multiple sensors.
- Ensure you use the most recently downloaded activation package.
- If the activation package is not available, generate a new one.
- The activation package contains sensitive information, you must handle it carefully and don’t share it with anyone.
-
SSH to the host on which the Cloud Connector Sensor is installed.
-
Copy the device-activation-package.json file downloaded from the NetWitness Cloud Portal to the /var/lib/netwitness/cloud-connector-server directory on the Cloud Connector Service host.
-
Navigate to the following directory, by running the command:
cd /var/lib/netwitness/cloud-connector-server
-
Change the user and group of the device-activation-package.json file to netwitness by executing the following command:
chown netwitness:netwitness device-activation-package.json
-
To verify if Cloud Connector Sensor is connected successfully, log in to the NetWitness Cloud Portal, and go to Sensor List and check if the sensor appears as Cloud Connector with connected status.
See also
Install Insight Sensor
3.3 - Uninstall Insight Sensor
Provides information about how to uninstall Insight Sensor.
If you have Insight Sensor installed and no longer want to use it, perform the following steps to uninstall it.
To uninstall the Insight Sensor, you must first remove the Insight Sensor from the NetWitness Cloud Portal and then uninstall the Insight Sensor on the NetWitness Platform.
Step 1: Remove the Insight Sensor from the NetWitness Cloud Portal
-
Log in to the NetWitness Cloud Portal.
-
Go to  Admin > Sensors > Sensor List.
Admin > Sensors > Sensor List.
-
Select the Insight Sensor that you want to delete using the Host Name and click Remove Sensor.
A confirmation pop-up is displayed.
-
Click Remove Sensor.
Step 2: Uninstall the Insight Sensor on the NetWitness Platform
-
Log in to the NetWitness Platform.
-
Navigate to  Admin > Services.
Admin > Services.
-
In the Services list, select the NetWitness Insight service and click  > View > Explore.
> View > Explore.
The Explore view for the NetWitness Insight service is displayed.
-
On the Explore view, in the left panel, click cloud > right-click Properties, select stop from the drop-down, and click Send.
-
Navigate to the Services list view, select the NetWitness Insight service and click  > Delete.
> Delete.
A confirmation pop-up is displayed.
-
Click Yes.
-
SSH to the Packet Decoder host on which the NetWitness Insight service is installed.
-
Run the following command to stop the Insight service:
-
Run the following command to get the Insight RPM package name:
rpm -qa | grep rsa-nw-cloud
The rpm package name will be displayed. For example, rpm -e rsa-nw-cloud-12.3.0.0-12746.5.b9d72db10.el7.x86_64
-
Run the following command to uninstall:
rpm -e <rpm package name>
Replace <rpm package name> with the actual rpm package name.
For example, rpm -e rsa-nw-cloud-12.3.0.0-12746.5.b9d72db10.el7.x86_64
-
Run the following command to remove the cloud config file:
rm -f /etc/netwitness/ng/cloud-aws.json
See also
3.4 - Uninstall Cloud Connector Sensor
Provides information about how to uninstall Cloud Connector Sensor.
If you have a Cloud Connector Sensor installed and you no longer want to use it, perform the following steps to delete the Cloud Connector Sensor.
To delete the Cloud Connector Sensor, you must first remove the Cloud Connector Sensor from the NetWitness Cloud Portal and then uninstall the Cloud Connector Sensor on the NetWitness Platform.
Step 1: Remove the Cloud Connector Sensor from the NetWitness Cloud Portal
-
Log in to the NetWitness Cloud Portal.
-
Go to  Admin > Sensors > Sensor List.
Admin > Sensors > Sensor List.
-
Select the Cloud Connector Sensor you want to delete and click Remove Sensor.
Step 2: Uninstall the Cloud Connector Sensor on the NetWitness Platform
-
SSH to the Admin Server.
-
Execute the following command:
/var/lib/netwitness/cloud-connector-server/nwtools/uninstall-cloud-connector.sh
-
Log in to the NetWitness Platform and go to  Admin > Services to verify if the Cloud Connector Sensor is removed.
Admin > Services to verify if the Cloud Connector Sensor is removed.
See also
Install the Cloud Connector Sensor
3.5 - Locate the Device ID for a Specific Insight Sensor
Provides information about how to locate the device ID for a specific Insight Sensor.
In case of multiple NetWitness Insight Sensor deployments, you will require the device ID if you want to delete or check the status of a specific Insight Sensor. You need to open the Insight Sensor host (Packet Decoder) on the Services page and find the device ID in Explore view on the NetWitness Cloud Portal user interface.
To locate the device ID for a specific Insight Sensor
-
Log in to the NetWitness Platform.
-
Go to  Admin > Services.
Admin > Services.
-
In the Services list, search NetWitness Insight in the Filter field.
-
Select the NetWitness Insight service and click  > View > Explore.
> View > Explore.
The Explore view for the NetWitness Insight service is displayed.
-
On the left panel, click sys > stats. The UUID and other information are displayed on the right panel.
The UUID value contains the complete 36-characters service ID of the Packet Decoder service.
The last 12-characters of the UUID are the Device ID of that Insight sensor.
For example, if the UUID of the Packet Decoder service is 399f9fa3-c100-4171-837f-d449c896d47b, the device ID of the sensor is d449c896d47b.
See also
3.6 - Enable or Disable the Cloud Connector Sensor
Provides information on how to Enable and Disable the Cloud Connector Sensor.
The Cloud Connector Sensor is installed on the Admin Server, allowing it to obtain asset data from the NetWitness Cloud and transfer it to on-premises services like Springboard and Context Hub. If you need to perform maintenance on the Cloud Connector Sensor, you can temporarily disable it. Disabling the Cloud Connector sensor will prevent on-premises services from retrieving NetWitness Cloud analytics and receiving alerts generated by NetWitness Cloud.
Disabling the Cloud Connector Sensor
- Users who have registered for NetWitness Cloud Portal will be notified by email whenever a sensor is disabled or enabled.
- If the Cloud Connector sensor is disabled, the following on-premises services will be unable to retrieve data from the cloud:
- Springboard
- Context Hub
- Context Highlights – Network Exposure information will not be shown.
- Network Behavior Panel
- Insight cloud alerts will not be delivered until the Cloud Connector sensor is enabled again.
Procedure
-
Log in to the NetWitness Cloud Portal.
-
Go to  Admin > Sensors List.
Admin > Sensors List.
-
Select the sensor and click Disable Sensor.
A confirmation pop-up is displayed.
-
Click Disable Sensor.
Enabling the Cloud Connector Sensor
Users who have registered for NetWitness Cloud Portal in an environment will be notified by email whenever a sensor is enabled.
Procedure
-
Log in to the NetWitness Cloud Portal.
-
Go to  Admin > Sensors List.
Admin > Sensors List.
-
Select the sensor and click Enable Sensor.
A confirmation pop-up is displayed.
-
Click Enable Sensor.
See also
3.7 - Enable or Disable the Insight Sensor
Provides information on how to Enable and Disable the Insight Sensor.
The Insight Sensor is installed on the Packet Decoder, allowing it to capture and transfer the network metadata to the NetWitness Cloud. If you need to perform maintenance on the Insight Sensor, you can temporarily disable it. Disabling the Insight sensor will prevent it from metadata capture, and data transfer is paused.
NoteFrom NetWitness Platform version 12.4 or later, users who have registered for NetWitness Cloud Portal will be notified by email whenever a sensor is disabled or enabled.
Important
Before you begin, verify your Insight Sensor version. Navigate to the Sensor List tab and check the version listed within the Sensor Version column.
- If your Insight sensor version is 12.3 or 12.3.1, you must perform steps 1-9 to disable or enable the sensor.
- If your Insight sensor version is 12.4 or later, you can proceed directly to steps 5-9 to disable or enable the sensor.
To Disable the Insight Sensor
-
Log in to the NetWitness Cloud Portal.
-
Go to  Admin > Sensors List.
Admin > Sensors List.
-
Select the sensor and click Disable Sensor.
A confirmation pop-up is displayed.
-
Click Disable Sensor.
-
Log in to the NetWitness Platform.
-
Navigate to  Admin > Services.
Admin > Services.
-
In the Services list, select the NetWitness Insight service and click  > View > Explore.
> View > Explore.
The Explore view for the NetWitness Insight service is displayed.
-
On the Explore view, in the left panel, click cloud > right-click Properties, select stop from the drop-down, and click Send.
-
To stop the data auto aggregation, click cloud > config and set the parameter Aggregate Autostart (aggregate.autostart) to off.
To Enable the Insight sensor
-
Log in to the NetWitness Cloud Portal.
-
Go to  Admin > Sensors List.
Admin > Sensors List.
-
Select the sensor and click Enable Sensor.
A confirmation pop-up is displayed.
-
Click Enable Sensor.
-
Log in to the NetWitness Platform.
-
Navigate to  Admin > Services.
Admin > Services.
-
In the Services list, select the NetWitness Insight service and click  > View > Explore.
> View > Explore.
The Explore view for the NetWitness Insight service is displayed.
-
On the Explore view, in the left panel, click cloud > right-click Properties, select start from the drop-down, and click Send.
-
To start the data auto aggregation, click cloud > config and set the parameter Aggregate Autostart (aggregate.autostart) to on.
See also
3.8 - Configure Insight as a Data Source
Provides information about how to configure Insight data source
You can configure Insight as a data source for Context Hub and use the Context Hub server to fetch contextual information from NetWitness Insight. Use the following procedure in this topic to add Insight as a data source for Context Hub service and configure the settings for NetWitness Insight.
Prerequisities
Before you configure the Insight data source, ensure that:
- NetWitness Platform is in version 12.3 or later.
- Context Hub service is available in
 (Admin) > Services view of NetWitness Platform.
(Admin) > Services view of NetWitness Platform.
- Insight Sensor is installed and configured.
- Cloud Connector Sensor is installed and configured.
To add Insight as a data source for Context Hub
-
Log in to the NetWitness Platform.
-
Go to  (Admin) > Services.
(Admin) > Services.
The services view is displayed.
-
Select the Context Hub service and click  > View > Config.
> View > Config.
The Services Config View of Context Hub is displayed.
-
In the Data Sources tab, click  > Insight.
> Insight.
The Add Data Source dialog is displayed.
The required fields to configure the Insight data source are automatically updated.
-
Provide the following information:
-
By default, the Enable checkbox is selected. If this option is unchecked, you cannot add the data source or view the contextual information.
-
(Optional) Name: The name that identifies the data source and is automatically taken as Cloud-Connector-server. You can change the name.
NetWitness recommends keeping the default name which comes from the data source.
-
(Optional) Max. Concurrent Queries: You can configure the maximum number of concurrent queries to be run
against the configured data sources. The default value is 10.
-
Click Test Connection to test the connection between Context Hub and the NetWitness Insight.
-
Click Save.
Insight is added as a data source for Context Hub and is displayed in the Data Sources tab.
Next steps
After completing the configuration, you can view the contextual data in the Context Summary Panel for the Asset in the Respond or Investigate > Events view. For more information, see View Contextual Information for an Asset.
See also
3.9 - Enable Insight Incident Rules
Provides information on how to Enable the Insight Incident Rules.
By default, the NetWitness Insight Incident rules are disabled in your environment. You can enable them to generate the incident IDs for the alerts and customize the NetWitness Insight Incident Rules settings.
To Enable Insight Incident Rules
-
Log in to the NetWitness Platform.
-
Go to  (Configure) > Incident Rules.
(Configure) > Incident Rules.
-
Select the NetWitness Insight rule and click Enable.
A confirmation pop-up is displayed.
-
Click OK.
See also
3.10 - Monitor the Health of the Insight Sensor
Provides information about how to monitor the health of the Insight Sensor
NetWitness Cloud Portal allows you to visualize the health of the sensors deployed in your environment using the new Health And Wellness dashboard. Health and Wellness helps monitor sensor health and visualize the historical analytics and performance trends for all Insight sensors. It also helps isolate the problematic sensors.
Keeping track of the following parameters from Insight Sensor allows you to monitor Sensor health:
To access the Insight Sensor Health And Wellness Dashboard:
NoteThe displayed tenant name and region are based on the tenant deployment.
-
Log in to the NetWitness Insight.
-
Go to  Admin > Health And Wellness.
Admin > Health And Wellness.
The Health and Wellness dashboard is displayed and consists of two widgets with different metrics.
-
Select the Date Range from the drop-down list. The information displayed in each graph is updated accordingly. The last 7 days’ data is displayed by default. Using the Date Range drop-down list, you can view the metrics of the Last 7 Days, Last 2 Weeks, Last Month, Last 3 Months, or Last 6 months.
-
You can also view the same data in a tabular format. Click  (toggle) within each widget. When the tabular format is turned ON. You can perform the following operations on the widget:
(toggle) within each widget. When the tabular format is turned ON. You can perform the following operations on the widget:
- You can navigate between pages using the page navigation options and view all the data seamlessly.
- You can select the number of data entries per page using the drop-down list located at the bottom of each widget. By default, 10 rows are displayed per page. However, you can modify the number of rows displayed per page.
- You can export the data in a .CSV format. To download the data, click Export.
Understand the Sensor Health and Wellness Dashboard Visualizations
| Visualization |
Metrics |
Description |
| Decoder Throughput |
Daily amount of data captured and processed by the decoder where the sensor is installed within the date range. |
The Daily throughput trend line is shown. You can see the trends for all Insight Sensors simultaneously, select a particular Insight Sensor, and analyze the trend. |
| Data Uploaded |
Total file sizes uploaded to NetWitness Cloud in the selected date range. |
The Daily Data uploaded trend line is shown. You can see the trends for all Insight Sensors simultaneously, select a particular Insight Sensor, and analyze the trend. |
See also
3.11 - Use Sensor Filters
Provides information on how to filter sensors in the Sensor List tab.
To better manage a large number of sensors, you can search and filter for specific sensors by any criteria in the list of sensors from the  Admin > Sensor List page in the NetWitness Cloud Portal UI.
Admin > Sensor List page in the NetWitness Cloud Portal UI.
To filter the sensors
-
Log in to NetWitness Cloud Portal.
-
Go to  Admin > Sensors > Sensor List.
Admin > Sensors > Sensor List.
-
Click Filter.
The Filter panel is displayed.
-
In the above panel, utilize one or more of the following options to filter the sensors:
-
Host Name: Specify the sensor’s host name to filter the sensor list. You can start typing the name of the host. Type one character and a list of sensors that contain that character is displayed, as you continue to type the list is filtered to match.
-
Status: Select one or more statuses from the drop-down menu. The available options are Connected, Disconnected, and Disabled.
-
Sensor Type: Select the type of sensor from the drop-down menu. For example, Insight Sensor.
Only one sensor can be selected at a time for filtering.
-
Sensor Version: Select one or more versions from the drop-down menu. For example, when you type the two characters (12 versions), and a list of sensors that contain those characters are displayed.
-
Click Apply Filter.
The sensors are displayed in the right panel according to the filter you selected. To clear filters, at the bottom of the left panel, click Clear.
See also
4 - Investigate
Provides information about how to monitor and perform investigation on assets.
4.1 - View Assets Data on Springboard
Provides information about viewing Assets data on the Springboard panel and do further analysis and investigation.
NetWitness Springboard provides analysts with visibility into all the behavior details of an asset in the form of asset data. These behavior details are based on cloud analytics performed by NetWitness Insight on uploaded network metadata by the Insight sensor.
The Springboard retrieves NetWitness Insight data results from the cloud leveraging the Cloud Connector sensor. With this data, analysts can create a new panel with data type Assets to monitor and identify risky assets in their environment, which helps in further investigation of an asset.
NoteBy default, the new asset panel will not appear in Springboard and you need to add the assets panel.
NoteDuring the initial setup, it may take up to 48 hours for analytics results to be displayed on the Springboard panel.
The assets IP are categorized based on the Network Exposure. The critical ones are highlighted with red with a severity ranging from 76 to 100 and 100 is the maximum, which requires immediate attention.
Note
An administrator must provide the appropriate permissions to allow users to edit the springboard panels. For more information see the the Springboard section in the “Role Permissions” topic in the see topic
System Security and User Management Guide.
Analysts can perform the following actions on the Assets Panel:
-
Click an asset IP in the assets panel to view or investigate the assets details with relevant filters applied in the Investigate > Events view.
-
Click  at the top of the assets panel to view all the results in the Investigate > Events view.
at the top of the assets panel to view all the results in the Investigate > Events view.
-
Click a row in the table to view details or to investigate.
-
Change the time range for some panels namely Assets and Alerts panels. To change the time range, select the time range selection box from the drop-down menu in the top left corner of the Springboard view.
-
Scroll to view the different panels using the scroll bar  available below the panels.
available below the panels.
-
Click  to refresh and load the latest data into the panel.
to refresh and load the latest data into the panel.
To add the Assets panel
-
Log in to the NetWitness Platform.
-
Click  either on the top or on the right side of the view or click
either on the top or on the right side of the view or click  at the bottom of the view to add a panel.
at the bottom of the view to add a panel.
The Create New Panel dialog is displayed. The following figure is an example of the Assets panel configuration.
-
In the Input Settings section:
-
Name: Enter a unique name for the panel. The name can include letters, numbers, spaces, and special characters, such as _ - ( ) [ ].
-
Number of Results: By default, the number of results is 25. Specify the number of results that range from 25 to 100.
-
Data Type: Select the data type as Assets.
-
Data Source: Select the source of the data to use for the panel. You can use Broker or Concentrator to filter the query results on the Investigate > Events page for further investigation.
-
In the Output Settings section, select the appropriate settings based on the data type.
-
Click Add Panel.
-
Click Save Board once you have added all the panels.
For more information, see topic
Managing the Springboard.
See also
4.2 - View Contextual Information for an Asset
Provides information about viewing Contextual Information and Network Behavior of an asset and do further analysis and investigation.
NetWitness empowers analysts with the capability to perform context lookups for assets, accessible through the Investigate > Events and Respond pages. By leveraging Context Lookup, analysts can examine an asset’s Network Behavior and determine its criticality. Contextual information plays a pivotal role in enabling analysts to comprehend the asset’s value, evolving categorization, and associated behaviors. This information enables analysts to make informed decisions and take timely, appropriate actions throughout their analysis. The Context Lookup panel showcases contextual information related to the selected asset, with the available data based on the configured sources within the Context Hub.
To perform a Context Lookup for an Asset from the Events view
-
Log in to the NetWitness Platform.
-
Go to Investigate > Events.
-
On the Query search bar, enter the IP address of the asset you want to view the context data and click  to load events in the Events panel.
to load events in the Events panel.
A query is executed in the Events panel, and matching events are listed.
-
In the Events panel, left or right-click the IP address.
A Context Highlights dialog is displayed.
-
Click Network Exposure.
The Network Behavior panel of the asset is displayed.
The Network Behavior panel offers a comprehensive overview of an asset’s network activity, providing valuable insights for analysts seeking to understand its communication with other network assets. Using sparklines, analysts can quickly understand recent changes in network behavior over time. In addition, the panel provides contextual information, including exposure rank, categorization, and behavioral patterns, which serve as powerful tools for in-depth analysis, enabling the identification of potential risks and vulnerabilities associated with the asset.
The Network Behavior panel provides the following information about the asset:
Enterprise Network Exposure
The enterprise network exposure helps analysts determine asset criticality in relation to all other assets within the enterprise. It is determined by an in-built algorithm that calculates a rank for each asset, taking into account multiple factors, such as the number of services exported by the asset, as well as the quantity of internal and external IP addresses that connect to it. This enables the analysts to gain a comprehensive understanding of an asset’s significance within the enterprise network, allowing them to prioritize resources and make informed decisions accordingly.
The Enterprise Network Exposure has two values:
-
Exposure Rank Highlights
An asset’s rank is established by evaluating its exposure value, a metric derived from the combined analysis of the services it exposes and the volume of internal and external traffic it handles. This evaluation results in a rank that serves as an indicator of the asset’s criticality relative to all other assets within the network. Sparkline offers a concise overview of asset trends, enabling analysts to quickly identify whether rank is increasing, decreasing, or maintaining a consistent level. A lower rank indicates a higher level of criticality, highlighting the asset’s importance.
For example,
-
An asset with a rank of 10 / 200 means that the asset ranks 10th among 200 total assets, where 9 assets have a higher exposure than this asset, and 190 have lower exposure. This determination is influenced by a combination of the following factors:
- The asset might expose a lot of services compared to other assets.
- The asset might be handling a lot of traffic compared to other assets.
-
An asset with a rank of 190 / 200 means that the asset ranks 190th among 200 total assets, where 189 assets have a higher exposure than this asset, and 10 have lower exposure. This determination is influenced by a combination of the following factors:
- The asset might not expose a lot of services compared to other assets.
- The asset might not handle a lot of traffic compared to other assets.
-
Exposure Rank (Percentile)
The exposure rank percentile provides a valuable measure of an asset’s significance, represented as a percentile. This percentile reflects the asset’s level of criticality within the network. A higher percentile indicates a greater degree of criticality, highlighting the asset’s importance. For example,
-
An asset with an exposure value in the 90th percentile is regarded as having a high level of criticality. This means that the asset’s exposure is higher than 90% of all other assets and only 10% of assets have a higher exposure than this asset. This determination is influenced by a combination of the following factors:
- The asset might expose a lot of services compared to other assets.
- The asset might be handling a lot of traffic compared to other assets.
-
An asset with an exposure value in the 10th percentile is regarded as having a lower level of criticality. This means that the asset’s exposure is higher than only 10% of all other assets and that 90% of assets have a higher exposure than this asset. This determination is influenced by a combination of the following factors:
- The asset might not expose a lot of services compared to other assets.
- The asset might not handle a lot of traffic compared to other assets.
Peer Network Exposure
NoteA network peer group refers to a subset of assets within a larger network with similar characteristics and functionalities. For example, all the FTP servers in an organization would be considered a peer group.
The peer network exposure helps analysts in assessing asset criticality, similar to the Enterprise Network Exposure, but with a focus on assets within the asset peer group. A dedicated in-built algorithm is used to determine the peer network exposure rank for each asset, taking into consideration its relation to assets of the same type and category. The rank calculation is based on factors such as the number of services exported by the asset and the count of internal and external IP addresses that connect to these services. By leveraging this indicator, analysts gain insights into an asset’s relative criticality within its peer group, enabling them to prioritize resources and make informed decisions accordingly.
The peer network exposure has two values:
-
Exposure Rank Highlights
The rank of an asset within a group of assets sharing the same type and category is determined by evaluating the asset’s level of exposure in comparison to all other asset IPs within the peer group. Sparkline offers a concise overview of asset trends, enabling analysts to quickly identify whether rank is increasing, decreasing, or maintaining a consistent level. A lower rank signifies a higher level of importance within the peer group, indicating that the asset has a more significant presence and impact compared to others in the same category.
For example,
-
An asset with a rank of 10 / 200 means that the asset ranks 10th among 200 peer assets, where 9 assets have a higher exposure than this asset, and 190 have lower exposure. This determination is influenced by a combination of the following factors:
- The asset might expose a lot of services compared to other assets within its peer group.
- The asset might be handling a lot of traffic compared to other assets in its peer group.
-
An asset with a rank of 190 / 200 means that the asset ranks 190th among 200 peer assets, where 189 assets have a higher exposure than this asset, and 10 have lower exposure. This determination is influenced by a combination of the following factors:
- The asset might not expose a lot of services compared to other assets within its peer group.
- The asset might not handle a lot of traffic compared to other assets in its peer group.
-
Exposure Rank (Percentile)
The exposure rank percentile provides a means to evaluate the criticality of an asset by comparing it to other assets within its peer group that share the same type and category. Expressed as a percentile, it reflects the asset’s level of criticality relative to other assets. A higher percentile indicates that the asset is more critical compared to other assets in the same group.
For example,
-
An asset with an exposure value in the 90th percentile is regarded as having a high level of criticality. This means that the asset’s exposure is higher than 90% of all other peer assets and only 10% of assets have a higher exposure than this asset. This determination is influenced by a combination of the following factors:
- Asset might expose a lot of services compared to other assets in its peer group.
- Asset might be handling a lot of traffic compared to other assets in its peer group.
-
An asset with an exposure value in the 10th percentile is regarded as having a lower level of criticality. This means that the asset’s exposure is higher than only 10% of all other peer assets and that 90% of assets have a higher exposure than this asset. This determination is influenced by a combination of the following factors:
- The asset might not expose a lot of services compared to other assets in its peer group.
- The asset might not handle a lot of traffic compared to other assets in its peer group.
Peer Network Activity
Note
-
A network peer group refers to a subset of assets within a larger network with similar characteristics and functionalities. For example, all the FTP servers in an organization would be considered a peer group.
-
The activity rank of an asset is defined only if the asset has a defined category. Assets of type Undefined, Client, MSMC, MSSC, and MSFC do not have a defined category and, therefore, will not have an activity rank relative to the peer group.
The peer network activity rank evaluates the level of asset popularity within its peer group. Asset activity is determined using a dedicated in-built algorithm that takes into account the total number of unique IP addresses connecting to the asset in relation to its peers.
The peer network activity has two values:
-
Activity Rank Highlights
The activity rank of an asset is determined by its popularity among its peer group. Sparkline offers a concise overview of asset trends, enabling analysts to quickly identify whether rank is increasing, decreasing, or maintaining a consistent level. Rank is calculated using the in-built algorithm that considers the total number of unique client IPs making requests for services associated with the peer group that the asset belongs to.
For example,
-
An asset with a rank of 10 / 200 means that the asset ranks 10th among 200 peer assets, where 9 peer assets have higher activity levels than this asset, and 190 have lower activity levels. This determination is influenced by the following factor:
- The total number of unique IP addresses connecting to the asset.
-
An asset with a rank of 190 / 200 means that the asset ranks 190th among 200 peer assets, where 189 peer assets have higher activity levels than this asset, and 10 have lower activity levels. This determination is influenced by the following factor:
- The total number of unique IP addresses connecting to the asset.
-
Activity Rank (Percentile)
The activity rank percentile provides a percentile-based measure to evaluate the level of activity displayed by an asset within its peer group. It serves as a valuable tool for understanding the importance of an asset within its peer group. A high activity rank percentile indicates that the asset is more active in comparison to other assets in the same peer group.
For example:
-
An asset with a value in the 90th percentile indicates a high level of activity. This means that the asset’s activity is higher than 90% of all other peer assets and only 10% of assets have a higher activity than this asset.
-
An asset with a value in the 10th percentile indicates a relatively low level of activity. This means that the asset’s activity is higher than only 10% of all other peer assets and that 90% of assets have a higher activity than this asset.
Severity level for Asset
The asset severity is computed for Enterprise Network Exposure, Peer Network Exposure, and Peer Network Activity. The Asset Severity relates to the critical, high, medium, and low scores. Following is a summary of asset severity scores.
| Severity |
Color |
Rank |
| Low |
Green |
1-25 |
| Medium |
Yellow |
26-50 |
| High |
Orange |
51-75 |
| Critical |
Red |
76-100 |
Overview
The Overview section provides the following parameters:
Asset Type: Indicates the device type associated with the asset, determined based on the number of exported services and the volume of network traffic it handles. An asset can be categorized as one of the following types: Client, Server, FewClients, Many Services Few Clients (MSFC), Many Services Some Clients (MSSC), Many Services Many Clients (MSMC), or Undefined.
Asset Types
The type of asset is determined by evaluating the network profile that has been calculated for the asset.
| Asset Type |
Description |
| Client |
An IP address that does not export services to other IPs. |
| Server |
An IP address that exports services to other IPs. Insight assigns Server as an asset type if any one of the following conditions is met:
- At least one of the exported services handles at least 50 % of the total traffic and asset serviced five or more clients.
- At least two of the exported services handle at least 60% of the traffic together and asset serviced for five or more clients. |
| FewClients |
An IP address that export services to a few other IP addresses. Insight assigns FewClients as an asset type based on the following criteria.
- At least one of the exported services handles at least 50% of total traffic and asset serviced for up to four clients. |
| Many Services Few Clients (MSFC) |
An IP address that has a large number of services exported to a few clients. Insight assigns MSFC as an asset type based on the following criteria.
- The asset exports more than 20 services and serviced up to four clients. |
| Many Services Some Clients (MSSC) |
An IP address that has a large number of services exported to some clients. Insight assigns MSSC as an asset type based on the following criteria.
- The asset exports more than 20 services and serviced up to 19 clients. |
| Many Services Many Clients (MSMC) |
An IP address that has a large number of services exported to many clients. Insight assigns MSMC as an asset type based on the following criteria.
- The asset exports more than 20 services and serviced 20 or more clients. |
| Undefined |
An IP address that exports a variety of random services to a variable number of IP addresses. |
Asset Category: The asset category is determined by the distribution of traffic reaching the asset. An asset can expose many port numbers identifying specific services. The IANA Service Name and Transport Protocol Port Number Registry provide a list of well-known port numbers and their associated services.
For example, an asset that exports services to traffic on ports 80 and 443 could have a category value of HTTP and HTTPS.
NoteAn asset can have one or more categories.
First Time Seen: Displays the timestamp when the analytics first observed an asset.
Last Time Seen: Displays the timestamp when the analytics last observed an asset.
Highlights
The Highlights section provides a quick high-level overview of the last observed asset changes on the network.
NoteThe asset will always display all available data for the past 7 days in the UI.
Exposed Services: Displays the current number of active services for an asset. An asset can expose multiple services, such as HTTPS and SSH. The number of services exposed by an asset can change over time. The sparkline is a trend of the recently observed number of exposed services by the asset. If you hover over the sparkline, you can view the trending numbers.
For example, NetWitness Insight detected the following exposed services for the asset 10.0.0.0 over the past four days:
- January 1, 2023: 1 service (FTP)
- January 2, 2023: 1 service (FTP)
- January 3, 2023: 1 service (FTP)
- January 4, 2023: 2 services (FTP, SMTP)
In this example, the sparkline will show a slight increase in trend. The number 2 next to the sparkline chart is the last observed number of exposed services for this asset. In this case, the asset exposed FTP for a duration of 3 days, and then NetWitness Insight detected that SMTP was added to list of exposed services.
External Connections: Displays the number of external clients that request services from the asset. The sparkline is a trend of the observed number of external clients that requested services exported by the asset. If you hover over the sparkline, you can view the trending numbers.
For example, NetWitness Insight detected the following number of external connections established with the asset 10.0.0.0 over the past three days:
- January 1, 2023: 0 connections
- January 2, 2023: 2 connections
- January 3, 2023: 5 connections
In this example, the sparkline will show an increasing trend. The number 5 next to the sparkline chart is the last observed number of external connections for this asset.
Connection Types: Displays the number of services used by external clients. The sparkline displays a trend of the recently observed total number of services used by external clients. If you hover over the sparkline, you can view the trending numbers.
For example, NetWitness Insight detected the following number of services provided by asset 10.0.0.0 used by external clients over the past three days:
- January 1, 2023: 3 services (HTTP, HTTPS, SSH)
- January 2, 2023: 3 services (HTTP, HTTPS, SSH)
- January 3, 2023: 5 services (HTTP, HTTPS, SSH, FTP, SFTP)
In this example, the sparkline will show an increasing trend. The number 5 next to the sparkline chart is the last observed number of services used by external clients.
Connection Anomalies: Displays the total number of connections to external IPs using unrecognized TCP/UDP traffic. Unrecognized traffic does not match any of the known protocols.
The sparkline displays a trend of the recently observed total number of external sources and destinations for unrecognized TCP/UDP traffic. If you hover over the sparkline, you can view the trending numbers.
For example, NetWitness Insight detected the following number of unrecognized connections from 10.0.0.0 over the past five days:
- January 1, 2023: 3 connections
- January 2, 2023: 3 connections
- January 3, 2023: 7 connections
- January 4, 2023: 5 connections
- January 5, 2023: 4 connections
In this example, the sparkline shows an initially increasing trend that peaked at 7 connections and is now decreasing. The number 4 next to the sparkline chart is the last observed number of connections to external IPs using unrecognized TCP/UDP traffic.
Historical Service Trend
The Historical Service Trend displays how much traffic the asset serves out of the total traffic that is captured per service over time. The Historical Service Trend can help analysts understand why an asset is defined as a certain category type. By examining the percentage of services shared by the asset, analysts can better understand its role and purpose. Observing how the service percentages evolve over time provides perspective on any shifts in the asset category. This information empowers analysts to make informed decisions without the need for extensive additional research, enhancing their analytical efficiency.
For example, if a server receives 60% of the total DNS traffic, this value plays a significant role in determining the asset category for that server.
To better understand the traffic volume of different services, services in the chart legend are sorted from highest enterprise traffic to lowest enterprise traffic using the latest date data. In cases where services have the same percentage value, the services are sorted alphabetically as a secondary sort. The chart legend makes it easy to identify which services have the highest and lowest traffic volume.
Analysts can perform the following actions on the Historical Service Trend chart:
-
Hover over a data point on the chart to reveal the shared services percentage.
-
Click  to navigate to the next page to view the other services available.
to navigate to the next page to view the other services available.
-
Analysts can use the service filter feature with the searchable drop-down menu to filter services by multiple values at once. This allows you to compare different services and gain valuable insights from your data. For example, you can filter HTTP and DNS services and easily understand your data.
-
Analysts can navigate seamlessly between the first and last pages using the pagination option. To go to the last page, click  .
.
NoteThe asset will always display all available data for the past 7 days in the UI.
See also
4.3 - View Insight Alerts from Respond View
Provides information about viewing Insight alerts from the Respond view and do further analysis and investigation.
Analysts can view NetWitness Insight’s alerts based on Asset category change over time and New asset discovered in the environment. The alerts are listed on the Respond > Alerts page.
| Alert Type |
Description |
| Asset category change over time |
NetWitness Insight introduces a new alert named Asset category change over time. This feature establishes a baseline for an asset’s category and monitors the asset for any category changes. If there is a change in the asset category after the same category was observed for 7 consecutive days, NetWitness Insight will generate an alert for that particular asset.
If the category of an asset changes over time, it means that the purpose of the asset has been altered. For example, if an asset serves as an HTTP server for a week and then suddenly changes into a DNS server, there could be several reasons for this change. It could be a configuration modification made by the administrator, or the asset has been compromised by an unauthorized person who gained access to the network and altered the asset. |
New asset discovered in environment
(Available in BETA mode) |
NetWitness Insight introduces a new alert named New asset discovered in environment from the 12.3.1 version or later. This alert will be generated whenever a new asset Server type is detected in the environment for the first time or if an existing asset has not been observed by NetWitness Insight for the last 30 days. This alert is generated for assets identified as server by NetWitness Insight. This feature enhances visibility and provides analysts with an improved understanding of the assets present in the environment.
Note-This alert is generated only for assets identified as Server, FewClients, Many Services Few Clients, Many Services Some Clients, and Many Services Many Clients. An alert will not be generated for assets identified as Client and Undefined types.
-NetWitness recommends that you enable this feature only after you have deployed all the sensors. If you add a new sensor after the feature is enabled, Insight will consider all the servers observed only from that sensor as new assets and generate new alerts for them. |
| Alert Type |
Description |
| Asset category change over time |
NetWitness Insight introduces a new alert named Asset category change over time. This feature establishes a baseline for an asset’s category and monitors the asset for any category changes. If there is a change in the asset category after the same category was observed for 7 consecutive days, NetWitness Insight will generate an alert for that particular asset.
If the category of an asset changes over time, it means that the purpose of the asset has been altered. For example, if an asset serves as an HTTP server for a week and then suddenly changes into a DNS server, there could be several reasons for this change. It could be a configuration modification made by the administrator, or the asset has been compromised by an unauthorized person who gained access to the network and altered the asset. |
New asset discovered in environment
(Available in BETA mode) |
NetWitness Insight introduces a new alert named New asset discovered in environment from the 12.3.1 version or later. This alert will be generated whenever a new asset Server type is detected in the environment for the first time or if an existing asset has not been observed by NetWitness Insight for the last 30 days. This alert is generated for assets identified as server by NetWitness Insight. This feature enhances visibility and provides analysts with an improved understanding of the assets present in the environment.
Note-This alert is generated only for assets identified as Server, FewClients, Many Services Few Clients, Many Services Some Clients, and Many Services Many Clients. An alert will not be generated for assets identified as Client and Undefined types.
-NetWitness recommends that you enable this feature only after you have deployed all the sensors. If you add a new sensor after the feature is enabled, Insight will consider all the servers observed only from that sensor as new assets and generate new alerts for them. |
By default, NetWitness Insight generates alerts based on two priority levels. However, the priority level can be changed by using the incident rule:
- Low-priority alerts for asset change for clients
- Medium priority alerts for asset change for servers
This provides valuable insights to analysts when considering the asset’s profile. By observing such changes, analysts can better understand the potential implications and take appropriate actions to protect the network.
View Insight Alerts Details
In the Alerts List view, you can browse the Insight alerts from the NetWitness Insight source, filter them, and group them to create incidents. This procedure shows you how to access the Insight alerts list.
To View Insight Alert Details
-
Log in to the NetWitness Platform.
-
Go to Respond > Alerts. The Alerts List view displays a list of all NetWitness alerts.
-
In the Filters panel, under the Source options, select NetWitness Insight.
NoteYou can change the time range to filter them and view alerts.
All the alerts related to NetWitness Insight are listed.
Clicking on the Alert Name takes you to the Overview page with the following details. The following figure represents Asset category change over time alert.
The following figure represents New asset discovered in environment alert.
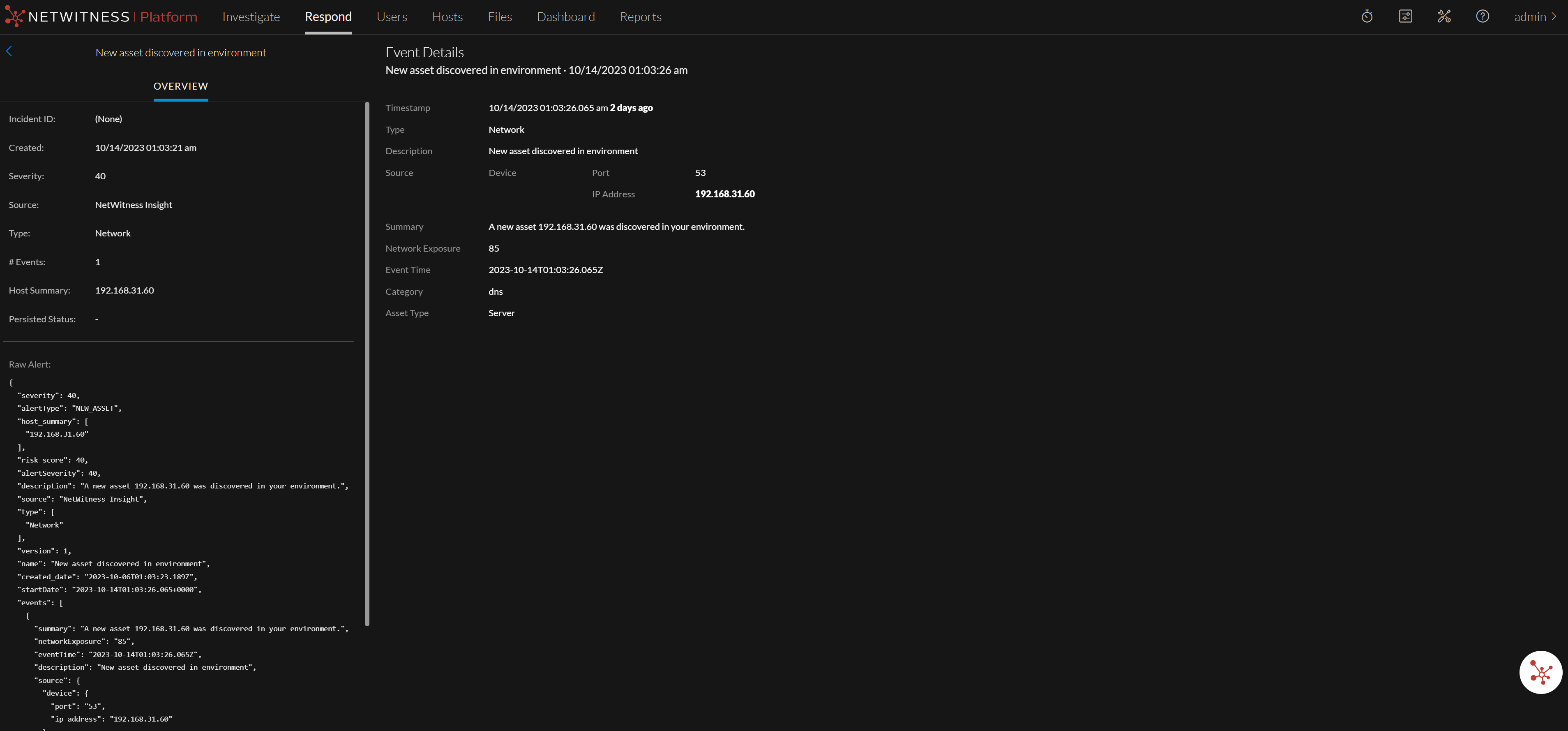
| Column |
Description |
| Incident ID |
Displays the Incident ID of the alert. If there is no incident ID, the alert does not belong to any incident, and you can create an incident to include this alert or add the alert to an existing incident.
NoteInsight alerts will have no Incident IDs by default and will be displayed as (None). You need to enable the Incident Rules to start generating the Incident IDs. For more information, see the topic Enable Insight Incident Rules. |
| Created |
Displays the date and time when the alert was recorded in the source system. |
| Severity |
Displays the level of severity of the alert. The values are from 1 through 100. In this case, the severity is 40 for medium Insight alerts. |
| Source |
Displays the source of the alert. In this case, the source of the alert is NetWitness Insight. |
| Type |
Displays the type of events in the alert. In this case, the type of event is Network. |
| # Events |
Displays the number of events contained within an alert. NetWitness Insight alerts always have one Event. |
| Host Summary |
Displays details of the IP, like the IP from where the alert was triggered. |
| Persisted status |
Displays the persistent status of the Incident. In this case, it is None (-). |
| Raw Alert |
Displays the raw alert metadata. |
| Timestamp |
Displays the time when the alert was generated. |
| Type |
Displays the type of events in the alert. In this case, the type of event is Network. |
| Description |
Displays a basic description of the alert. In this case, it is Asset category change over time. |
| Port |
Displays the port numbers used by the asset to service network traffic. In this case, it is 53, 443. |
| IP Address |
Displays the IP address of the asset for which the alert was detected. You can either left or right-click this IP address and view the Context Highlights and Network Behavior. For more information, see the topic View Contextual Information for an Asset. |
| Summary |
Displays the summary of the asset. In this case, The asset 192.168.1.1 changed from category HTTP to category DNS, HTTPS after being category HTTP for 7 days. |
| Network Exposure |
Displays the asset network exposure value ranging from 1 to 100. In this case, the network exposure value is 45. For more information on network exposure, see the topic View Contextual Information for an Asset. |
| Prev Category |
Displays the previous category of the asset type. In this case, it is HTTP. |
| New Category |
Displays the new category of the asset. In this case, it is DNS, HTTPS. |
| Event Time |
Displays the time when the alert was generated. |
| Category Duration Baseline |
Displays the number of days observed for the asset category before the change. The default value is 7 consecutive days. |
| Asset Type |
Displays the type of asset. In this case, it is Server. |
For more information on managing alerts, see Reviewing Alerts topic in
NetWitness Respond User Guide.
See also
4.4 - View Insight Incidents Details
Provides information about viewing Insight incidents from the Respond view and do further analysis and investigation.
You can view and access extensive incidents in the Respond > Incidents view. This procedure shows you how to access the Insight Incidents list. You can filter this list to view only the Incidents of interest.
To View Insight Incidents Details
-
Log in to the NetWitness Platform.
-
Go to Respond > Incidents.
The following table describes the columns in the Incidents List.
| Column |
Description |
| Created |
Shows the creation date of the incident. |
| Priority |
Shows the incident priority. Priority can be Critical, High, Medium, or Low. For Insight Incidents, it is Low and Medium. |
| Risk Score |
Shows the incident risk score. The risk score indicates the risk of the incident as calculated using an algorithm and is between 0-100. 100 is the highest risk score. |
| ID |
Shows the automatically created incident number. Each incident is assigned a unique number that you can use to track the incident.
NoteBy default, Incident IDs will appear as (None). To generate Incident IDs, you must enable the Incident Rules. For more information, see the topic Enable Insight Incident Rules. |
| Name |
Shows the incident name. The incident name is derived from the rule used to trigger the incident. Click the link to go to the Incident Details view for the selected incident. For example, NetWitness Insight for Asset category change over time. |
| Status |
Shows the incident status. By default, for Insight, it will display new status. |
| Assignee |
Shows the team member currently assigned to the incident. |
| Alert |
Shows the number of alerts associated with the incident. An incident may include many alerts. A large number of alerts might mean that you are experiencing a large-scale attack. |
For more information on Incidents, see
NetWitness Respond User Guide.
See also
4.5 - Whitelist Insight Alerts from Respond View
Provides information about whitelisting Insight alerts from the Respond view.
From NetWitness Platform version 12.4 or later, administrators and analysts can whitelist unwanted and recurring Insight alerts generated in the Respond > Alerts view. This enhancement allows administrators and analysts to select values such as IP Address and Asset Type and define a Whitelist condition to prevent unwanted alerts from being generated for these values.
For example, an administrator may choose to whitelist all alerts generated from a specific IP address or asset type that is known to be secure or non-malicious. Once the whitelist condition is configured correctly, these alerts will no longer be generated, thus reducing traffic on the Respond > Alerts view.
To whitelist an Insight alert from the Respond View
-
Log in to the NetWitness Platform.
-
Go to Respond > Alerts.
The Alerts view is displayed.
-
Select an Insight alert and click More Actions > Whitelist Alert.
NoteYou can select only one alert at a time for whitelisting.
The Alert Whitelisting dialog for Insight is displayed.
-
Enter the name of the Whitelist.
-
Select the required values, such as IP Address, Asset Type, or a combination of both.
NoteA minimum of one value must be selected for the field.
-
Specify the reason for whitelisting in the Comments section.
-
Click Whitelist.
The Confirm Alert Whitelisting confirmation dialog is displayed.
-
Click Confirm Whitelist.
Manage the Whitelists
The Whitelist tab allows you to manage alerts you have chosen to whitelist. Both administrators and analysts can view, filter, and delete the whitelisted items from the Whitelist tab. Removing a whitelisted item will resume the generation of new matched alerts for previously excluded values, such as IP addresses or asset types, under the Respond > Alerts view.
NoteDeleting a selected Whitelist item will generate new matching alerts only for the selected values.
You can do the following operations with the Whitelist tab:
-
View whitelisted alerts: View a list of all the alerts you have whitelisted from generating alerts.
-
Delete whitelisted alerts: Remove specific alerts from the whitelist, enabling them to generate alerts again. This can be helpful if you no longer need to exclude those alerts.
-
Filter whitelisted alerts: Quickly find specific whitelisted alerts by using the filtering options.
Important
-
Analysts must have one of the following permissions to view the Whitelists tab in the Respond view:
-
respond-server.alert.delete
-
respond-server.alert.read
-
respond-server.alert.manage
-
respond-server.alertrule.manage
-
respond-server.alertrule.read
-
Analysts must have the respond-server.alert.read permission to view the whitelists item in Respond > Whitelists view and respond-server.alert.manage permission to delete the Whitelists item.
To delete the whitelisted items
-
Go to Respond > Whitelists.
The Whitelists view is displayed.
-
Select the Whitelist item and click Delete.
A confirmation pop-up is displayed.
-
Click Delete Whitelist.
The Whitelist item is deleted.
For more information on the Whitelists tab, see the topic
Whitelists List View in the NetWitness Respond User Guide for 12.4.
See also
5 - Release Information
Provides information about release details on Insight.
5.1 - What's New
Provides information about new features and enhancements for NetWitness Insight.
The following features and enhancements have been introduced in NetWitness Insight:
April 1, 2024
Introducing Sensor Health and Wellness Dashboard
A new Sensor Health and Wellness Dashboard has been introduced for NetWitness Insight to provide visibility into the health of the sensors and monitor their status. Each dashboard visualization will automatically be refreshed with the most recent data to manage the service efficiently. The last 6 months Insight Sensor data will be available for analysis.
The dashboard offers information and analysis regarding the following:
- Daily Decoder Throughput information of individual sensors and all sensors.
- Data uploaded for individual sensors and all sensors.
For more information, see topic Monitor the Health of the Insight Sensor.
March 14, 2024
Whitelist Insight Alerts in Respond View
Administrators and analysts can now whitelist unwanted and recurring Insight alerts generated in the Respond > Alerts view. This enhancement provides the ability to select specific values, such as IP Address and Asset Type, and define a Whitelist condition to prevent unwanted alerts from being generated for these values. Using this enhancement, analysts can streamline the alert management process by excluding specific IP addresses or asset types that are known to be reliable and secure. This optimization minimizes unnecessary alerts generated on the Respond > Alerts view, reducing the time and effort required to review and analyze alerts.
NoteEnsure the NetWitness Platform version is 12.4 or later to use this feature.
For more information, see topic Whitelist Insight Alerts from Respond View.
Email Notification Settings for Sensor Status
NetWitness now includes Email Notification preferences for Sensor Status. With this feature, administrators can choose to turn on or turn off email notifications as needed, giving them more control and flexibility in managing notifications.
For more information, see Configure Email Notification Preferences for Insight.
November 6, 2023
Detect New Assets in Insight (BETA)
NetWitness Insight introduces a new alert named New asset discovered in environment. This alert is generated on the Respond > Alerts page whenever a new asset Server type is detected in the environment for the first time or if an existing asset has not been observed by NetWitness Insight for the last 30 days. This alert is generated for assets identified as server by NetWitness Insight. This feature enhances visibility and provides analysts with an improved understanding of the assets present in the environment, enabling them to better protect them from any potential attacks.
This feature is currently available in BETA mode and is disabled by default. Please contact NetWitness Customer Support team to enable the feature.
NoteEnsure the NetWitness Platform version is 12.3.1 or later to use this feature.
For more information, see topic View Insight Alerts from Respond View.
Historical Service Trend Chart Improvements
The following improvements are made to Historical Service Trend chart in 12.3.1 version:
-
Added a new Service filter feature that allows you to filter services using a searchable drop-down menu. Analysts can now filter services by multiple values simultaneously, making it easier to compare services and discover insights.
-
Improved pagination functionality now allows analysts to navigate between the first and last pages seamlessly.
-
Services in the chart legend are sorted from highest to lowest enterprise traffic using the latest date data. When services have the same percentage value, they are sorted alphabetically.
For more information, see topic View Contextual Information for an Asset.
NoteEnsure the NetWitness Platform version is 12.3.1 or later to use these improvements.
November 2, 2023
Email Notification on Exceeding Daily License Usage
NetWitness Insight customers exceeding the daily license usage limit three or more times within the last 14 days will receive an email notification.
Email Notification Settings for License Usage
NetWitness introduces a new Email Notifications setting option on the NetWitness Cloud Portal. This feature enables administrators to manage email notification preferences for License Usage. With this feature, administrators can choose to turn on or turn off email notifications as needed, giving them more control and flexibility in managing notifications.
For more information, see Configure Email Notification Preferences for Insight.
Check NetWitness Cloud Services Operational Health Status
Users can check the operational health status and service availability of NetWitness Cloud Services such as UEBA, Insight, and Live on
NetWitness Statuspage. The operational health status indicates if all the services and integrations are operational or experiencing any disruptions. These disruptions may be caused by server maintenance activity, regional network outages, or cloud vendor outages. If there are any service disruptions, they are recorded as Incidents and displayed on the Statuspage.
In addition, users can subscribe to receive email or Slack notifications whenever an incident occurs, see
Check System Status.
September 6, 2023
Introducing NetWitness Insight
NetWitness Insight is a SaaS solution available as an extension for a NetWitness Network, Detection & Response (NDR) customer. NetWitness Insight is an advanced analytics solution that leverages unsupervised machine learning to empower the response of the Security Operations Center (SOC) team. NetWitness Insight continuously examines network data collected by the Decoder to discover, profile, categorize, characterize, prioritize, and track all assets.
NetWitness Insight identifies the assets in the enterprise to alert analysts of their presence. The discovered assets are automatically categorized into groups of similar servers and prioritized based on their network profiles. These assets are presented to analysts in a Springboard panel to guide them to focus on certain assets to protect their organization. Contextual information about the asset is available anywhere analysts interact with IP addresses in Respond and Investigate workflows. Incidents and alerts can be created based on asset changes.
This helps organizations to:
- Asset discovery and characterization.
- Monitor critical Assets.
- Leverage the security operations team to triage based on prioritization.
5.2 - Known Issues
Provides information on the known issues, component title, issue, and their workaround.
March 14, 2024
| Components |
Title, Problem and Workaround |
Fixed Date |
| Cloud Connector Sensor |
Title: Insight users with Cloud Connector Sensor may experience frequent sensor status updates, resulting in excessive sensor status notifications.
Issue: Insight users with Cloud Connector Sensor may experience frequent sensor status updates, resulting in a large number of notification emails regarding the connection and disconnection of Cloud Connector Sensor. Workaround: None |
|