This is the multi-page printable view of this section.
Click here to print.
Return to the regular view of this page.
Getting Started
Provides information on getting started with UEBA.
1 - Getting Started with NetWitness UEBA
Provides information to get started with NetWitness UEBA.
To onboard NetWitness UEBA, existing customers with NetWitness Platform version 11.5.2 or later can share their tenant administrative user details with the NetWitness Sales team. The NetWitness Sales team then onboards the first administrative user from your organization to kick-start the set up process. The administrative user then receives a welcome email that contains the NetWitness Cloud Portal access URL, a user name, and a temporary password. Ensure that you reset the password at the first login.
The following checklist includes the steps to set-up and use NetWitness UEBA:
Before you Begin
-
Ensure that you configure the actual time on the Cloud Link Service (Log Decoder Host). Sync the device Network Time Protocol (NTP) with the NTP service on the admin server. For more information on how to configure NTP Sever, see
Configure NTP Servers.
-
The host on which the Cloud Link Service will be installed needs to be connected to Amazon Web Services(AWS). This might require changes to your existing firewall rules. Hosts will need to connect to the IP ranges for the chosen deployment region. For more information on the current list of AWS IPs by region, see
AWS IP address ranges.
-
(Optional) Ensure that you configure the proxy settings from NetWitness Platform version 11.5.3 or later, before installing the Cloud link Service. For more information, see Configure the proxy for the Cloud Link Service.
After completing the set-up, you can perform several tasks to respond to threats reported by NetWitness UEBA. For more information, see Investigate.
See also
2 - Welcome to NetWitness UEBA
Provides information about NetWitness UEBA.
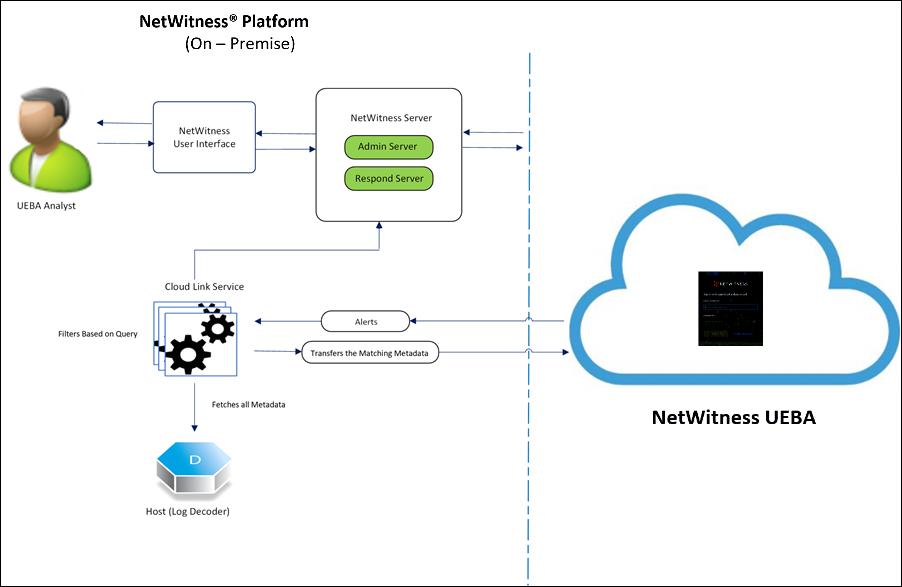
NetWitness UEBA is an add-on to NetWitness® Platform. The product is a SaaS service that analyzes NetWitness Platform data and triggers alerts on potential threats and malicious activity. NetWitness UEBA takes all the traditional functions of NetWitness UEBA (On-premises) and provides them as a native SaaS application. As a cloud service, UEBA has many additional benefits including operations from the Operations team who manage the service for your organization which enables NetWitness to release new content and enhancements faster so security teams are better equipped to respond to threats.
NetWitness UEBA is an advanced analytics and machine learning solution that leverages unsupervised machine learning and empowers Security Operations Center (SOC) teams to discover, investigate, and monitor risky behaviors in their environment. All users in an organization can be analyzed for abnormal user activities using log, and endpoint data already collected by your NetWitness Platform.
For existing NetWitness Platform customers, NetWitness UEBA enables analysts to:
- Detect malicious and rogue users
- Pinpoint high-risk behaviors
- Discover attacks
- Investigate emerging security threats
- Identify potential attacker’s activity
NetWitness UEBA resides on an Amazon Virtual Private Cloud (VPC) and each organization has its own VPC. If you have an on-premises NetWitness Platform deployment in your network, metadata will be uploaded to the cloud for analysis.
NetWitness UEBA performs advanced analytics on the data to enable analysts to discover potentials threats. Analysts will begin to see alerts and behavior profiles of users directly in their existing NetWitness Platform UI, and will be able to perform basic administration of the SaaS components from a dedicated SaaS UI.
See also
3 - NetWitness UEBA Use Cases
Provides information about what use cases does NetWitness UEBA address.
NetWitness UEBA focuses on providing advanced detection capabilities to alert organizations about suspicious and anomalous user behavior. These behaviors could represent a malicious insider abusing credentials and access or could represent an external threat actor exploiting compromised credentials and systems.
Identity theft typically begins with the theft of credentials, which are then used to obtain unauthorized access to resources and to gain control over the network. Attackers may also exploit compromised non-admin users to obtain access to resources for which they have administrative rights, and then escalate those privileges.
An attacker who uses stolen credentials might trigger suspicious network events while accessing resources. Detecting illicit credential use is possible, but requires the separation of attacker activity from the high volume of legitimate events. NetWitness UEBA helps you differentiate possible malicious activity from the otherwise abnormal, but not risky, user actions.
The use cases shown in the Understand the UEBA Alert Types list define certain risk types and the corresponding system capabilities used for their detection. It is important that you review the use cases, represented by their alert type and description, to gain an initial understanding of the related risky behavior of each use case.
Using NetWitness UEBA, you can then drill down into the indicators that reflect potential risky user activities to learn more. For more information about supported indicators, see Understand the UEBA Alert Types.
See also
4 - How NetWitness UEBA Works
Provides information about how NetWitness UEBA works.
The analytics engine in NetWitness® UEBA automatically monitors user behavior and utilizes advanced analytics to detect anomalies and risky behaviors. The analytics engine provides detailed analysis of user behavior, which enables analysts to review, investigate, monitor, and act on the identified risky behaviors.
The following table shows the steps that the alerting engine performs to derive the user behavioral results.
| Step |
Description |
|
| 1. |
Retrieve NetWitness Platform Data |
The analytics engine retrieves the raw event data and metadata keys From the Decoder/s by leveraging the Cloud Link Service in NetWitness® Platform. The analytics engine processes and analyzes this data to create analytic results. |
| 2. |
Create Baselines |
Baselines are derived from a detailed analysis of normal user behavior and are used as a basis for comparison to user behavior over time. An example of the baseline for a user can include information about the time a user typically logs in to the network. |
| 3. |
Detect Anomalies |
An anomaly is a deviation from a user’s normal baseline behavior. The analytics engine performs statistical analysis to compare each new activity to the baseline. User activities that deviate from the expected baseline values are scored accordingly to reflect the severity of the deviation. Anomalous activities are user behavior or abnormal user activities such as suspicious user logons, brute-force password attacks, unusual user changes, and abnormal file access. |
| 4. |
Generate Alerts |
The anomalies detected in the previous step are grouped into hourly batches by the username. Each batch is scored based on the uniqueness of its Indicators, which define validated anomalous activities. If the indicator composition is unique compared to a user’s historic hourly batch compositions, it is likely that this batch will be transformed into an alert and its anomalies into indicators. A high-scored batch of anomalies becomes an alert that contains validated indicators of compromise. |
| 5. |
Prioritize Users with Risky Behaviors |
The analytics engine prioritizes the potential risk from a user by using a simplified additive scoring formula. Each alert is assigned a severity that increases a user’s risk score by a predefined number of points. Users with high scores either have multiple alerts associated with them or they have alerts with high severity levels associated with them. |
See also
Identify Top Risky Users
5 - Access NetWitness UEBA
Provides information on how to access NetWitness UEBA.
In order to view a list of all users monitored by NetWitness UEBA, you need to have access to the NetWitness Platform User Interface.
To access NetWitness UEBA
-
Log in to NetWitness Platform.
-
Go to Users > Overview.
The user activity details are displayed.
See also
6 - Understand Sources Supported by Schema in UEBA Cloud
Provides information about various sources supported by schema in UEBA Cloud.
The topic provides a list of the various sources supported by schema in UEBA Cloud.
Authentication Schema
-
Windows Logon and Authentication Activity - Supported Event IDs: 4624, 4625, 4769, 4648 (device.type=winevent_snare|winevent_nic)
-
RSASecurID Token - device.type = ‘rsaacesrv’ ec.activity = ‘Logon’
-
RedHat Linux - device.type = ‘rhlinux’
-
Windows Remote Management - Supported Event IDs: 4624,4625,4769,4648 (device.type=windows)
-
VPN Logs - event.type = ‘vpn’ ec.activity = ’logon’
Note
- Please deploy the latest parsers from NetWitness Live to enable support for all the VPN devices.
- To support all VPN devices, ensure that the NetWitness Platform and Cloud Link Sensor versions are in 12.4 or later.
- NetWitness has tested and verified the functionality of Juniper, Citrix NetScaler, Palo Alto Networks, Cisco Adaptive Security Appliance (ASA) and Fortinet VPNs under the Authentication schema of UEBA. For any VPN to be considered under the Authentication module, the following metadata must be present in the respective VPN vendor’s logs:(event.type = ‘vpn’ && country.src exists && user.dst exists && ec.activity = ’logon’)
- Azure AD Logs - device.type = ‘microsoft_azure_signin_events’
NoteMake sure you have configured the Azure Monitor plugin in your deployment. This enables UEBA to run a query for Azure AD log events for monitoring purposes in the correct format. For more information on how to configure the Azure Monitor plugin, see the Azure Monitor Event Source Configuration Guide.
File Schema
-
Windows File Servers - Supported Event IDs: 4663,4660,4670,5145 (device.type=winevent_snare|winevent_nic)
-
device.type=windows
Active Directory Schema
-
Windows Active Directory - Supported Event IDs:
4670,4741,4742,4733,4734,4740,4794,5376,5377,5136,4764,4743,4739,4727,4728,4754,4756,4757,4758,4720,4722,4723,4724,4725,4726,4738,4767,
4717,4729,4730,4731,4732 (device.type=winevent_snare|winevent_nic)
-
device.type=windows
Endpoint Process Schema
- Endpoint Process - Category=‘Process Event’
Endpoint Registry Schema
- Endpoint Registry - Category=‘Registry Event’
See also
Identify Top Risky Users
7 - Log in to the NetWitness Cloud Portal
Provides information about how to access NetWitness Cloud Portal.
The NetWitness Cloud Portal provides administrators with the capability to manage and monitor UEBA services for their account.
Prerequisites
Before you log on to the NetWitness Cloud Portal, ensure that you have received an email from NetWitness containing the account URL link.
To log in to the NetWitness Cloud Portal
-
Click on the URL provided in the NetWitness Cloud Portal welcome email.
The NetWitness Cloud Portal home page is displayed.
-
Enter your registered email ID and the temporary password in the respective fields.
As this is your first login, the page prompts you to reset your password.
-
Enter the new password, and confirm the same.
Review the password format rules and ensure that your new password conforms to the indicated format rules.
-
Click Sign In.
See also
8 - Change NetWitness Cloud Portal Account Password for UEBA
Provides information on changing NetWitness Cloud Portal account password for UEBA.
Your NetWitness Cloud Portal account password is used for identification and authentication.
You can change your NetWitness Cloud Portal account password at any time. The password is valid for 90 days. Once the password is expired, you need to change your password. You can get an authentication code using your registered email address or your registered phone number.
If you have received a notification that your NetWitness Cloud Portal account password is about to expire, you must change your password.
Make sure that you enable Multi-Factor Authentication (MFA). To enable MFA, go to your Profile, and under Account Password, turn on Multi-Factor Authentication.
To change or reset your NetWitness Cloud Portal Account Password
-
In the NetWitness Cloud Portal login window, click Reset Password.
The Reset Password window is displayed.
-
Type the reset code that you received on your registered email address or phone number.
-
Type your new password.
-
Type your new password again to confirm.
-
Click Save.
See also
9 - Check System Status
Provides information about how to know the UEBA operational health status.
Users can check the operational health status or service availability of NetWitness UEBA including Cloud Link Service. The operational health status indicates if all the services and integrations are operational or experiencing any disruptions. The service disruptions may be caused by server maintenance activity, regional network outages, or cloud vendor outages. These service disruptions are recorded as Incidents and displayed on the Statuspage.
Users can also subscribe to receive email or Slack notifications whenever an incident occurs.
To Check the Health Status of NetWitness UEBA
-
Login to NetWitness Cloud Portal.
-
Click  (View System Status). The System Status tiles are displayed.
(View System Status). The System Status tiles are displayed.
- Sensors Status: Displays the connected or disconnected sensor count.
- Operational Health: Displays the operational health details for NetWitness UEBA. Status is indicated as below:
| Color |
Status |
| Green |
Indicates that NetWitness UEBA is operational |
| Yellow |
Indicates that Statuspage service is unavailable |
| Red |
Indicates that NetWitness UEBA is experiencing service disruptionsin the region it is deployed |
- If you observe that some services and/or integrations of NetWitness UEBA are non-operational or experiencing service disruptions, click on the Operational health status tile or visit
NetWitness Statuspage and learn more about service disruptions on the Statuspage.
Users can see the uptime of the past 90 days (across the regions) and the Incidents list on the Statuspage. If there is any recorded incident on a particular day, the status bar is displayed in red color. Click View historical uptime to see the service’s historical uptime beyond 90 days.
Subscribe to System Status Updates
Users can subscribe to receive email or Slack notifications whenever NetWitness Cloud Operations team creates, updates, or resolves an Incident for NetWitness UEBA.
To Subscribe to the System Status Updates
-
Click on the Subscribe to Updates on the NetWitness Statuspage.
NoteUsers will receive operational status notifications for all NetWitness Cloud Services upon subscription, regardless of licensed usage.
-
If you want to receive system status updates over an email, click  .
.
Enter the email address on which you want to receive notifications and click Subscribe via Email.
-
If you want to receive system status updates over Slack, click  .
.
Click Subscribe via Slack. You will be redirected to Sign in to your workspace slack page. Follow the online instructions and provide the required details to complete the sign-in and subscription process.
See also
Install Cloud Link Service
10 - About NetWitness UEBA licenses
Provides information about NetWitness UEBA licenses.
NetWitness UEBA licenses are subscription based licenses. The license entitlement is based on the number of users with a default data storage of 500 GB data storage capacity.
| License Type |
Limitations |
| NetWitness UEBA Subscription. This is based on the number of active user accounts monitored in your environment. |
Capacity limited to 500 GB per day of data storage. |
| NetWitness UEBA additional Daily Capacity Subscription. |
50 GB per day increments. |
See also
Setup and Manage NetWitness Administrators
11 - Setup and Manage UEBA Administrators
Provides information on how to set up and manage UEBA administrators.
Once the tenant administrative user of an organization is onboarded into NetWitness Cloud Portal, the administrative user can perform the following tasks:
- Manage other administrative users - add, delete, enable and disable administrators, and update the profiles.
- Install, configure, and manage sensors.
- Configure and manage multi-factor authentication (MFA) for administrators.
- Temporarily enable or disable access to other administrators, instead of deleting them permanently.
Use the following table as a guide to the user management tasks that you can perform.
User Management Tasks in NetWitness Cloud Portal
Add Additional Administrators
To add an administrative user
-
Go to  Admin > Users Management > Users.
Admin > Users Management > Users.
The Users and Roles page is displayed.
-
Click Add User.
The Add User window is displayed.
-
Enter your first name, last name, email ID, and mobile number in the respective fields.
-
Click Add.
Edit User Account Settings
As an administrator, you can update the user account settings for the administrators who are configured in the system. You must ensure that the contact information of administrative users is specified so that the user receives notifications on this contact number.
NoteThe mobile number you specify here must be valid as it will be used for multi-factor authentication for the user. For more information on multi-factor authentication, see Enable Multi-Factor Authentication for UEBA.
To edit the administrator account settings
-
Go to  Admin > Users Management > Users.
Admin > Users Management > Users.
The Users and Roles page is displayed.
-
Select the user, and click Edit Details.
The Edit Details page is displayed.
-
Edit the first name, last name, and mobile number of the user in the respective fields.
-
Click Save.
If you are logged in and you want to edit your contact information, update your user profile by going to
User Account > Profile.
Remove an Administrator
As an administrator, you can remove the account details and access privileges for other administrators.
To delete an administrator
-
Go to  Admin > Users Management > Users.
Admin > Users Management > Users.
The Users page is displayed.
-
Click Delete User.
Enable or Disable Access for Users
You can enable or disable access for users. When you disable access for a specific user, the user cannot access the NetWitness Cloud Portal account.
If a user is logged in to NetWitness Cloud Portal and the user access is disabled, the user can continue to access NetWitness Cloud Portal until the session times out.
To enable access for a user
- Log in to the NetWitness Cloud Portal.
- Go to
 Admin > Users Management > Users.
Admin > Users Management > Users.
- Under the Users tab, select a user and click Enable User.
- To confirm, click Enable.
To disable access for a user
- Log in to the NetWitness Cloud Portal.
- Go to
 Admin > Users Management > Users.
Admin > Users Management > Users.
- Under the Users tab, select a user and click Disable User.
- To confirm, click Disable.
See also
Install Cloud Link Service
12 - Enable Multi-factor Authentication for UEBA
Provides information on how to Enable Multi-factor Authentication for UEBA.
NetWitness offers Multi-factor authentication (MFA), using which you can configure an additional layer of credentials to secure your identity and manage access. If you enable MFA, then the administrative user will be prompted to additional identifications at the time of log in, such as verification code sent to the mobile number or mobile authentication application.
To Configure MFA
- Go to
 Admin > Account Settings > Multi-Factor Authentication.
The Multi-Factor Authentication page is displayed.
Admin > Account Settings > Multi-Factor Authentication.
The Multi-Factor Authentication page is displayed.
- Select ON, OFF or OPTIONAL as per your requirement.
The following table provides information on the different MFA settings that NetWitness Cloud Portal offers:
Multi-Factor Authentication Settings
| MFA Setting |
Description |
| ON |
Select ON to activate MFA. A secret code will be sent to the registered email account of the new administrators. Administrators can log in to their account, and choose between the secret code or an authentication mobile application as their preferred authentication method. |
| OFF |
Select OFF to deactivate MFA. Administrators can log in to their account with their registered email ID and password. |
| OPTIONAL |
Select OPTIONAL if you want to let the administrators decide if they want to activate or deactivate MFA for their accounts. |
See also
Cloud Link Service Overview
13 - Configure Email Notification Preferences for UEBA
Provides information on how to configure Email Notification preferences for UEBA.
NetWitness Cloud Portal introduces the Email Notifications setting option that allows administrators to manage email notification preferences for Sensor Status, Sensor Updates, and License Usage. Using this setting, administrators can choose to turn on or turn off email notifications as needed, giving them more control and flexibility in managing notifications.
Note
- By default, the email notifications for Sensor Updates and License Usage are enabled, and email is sent to the users registered to the NetWitness Cloud Portal.
- By default, the email notifications for Sensor Status are disabled, and emails related to sensor status are not sent to the users. However, you can enable these notifications anytime to start receiving them.
ImportantEnabling or disabling email notifications only affects the logged-in user, as it is not a global setting.
To Adjust the Email Notification Preferences
-
Log in to the NetWitness Cloud Portal.
-
Click on your name or avatar located in the top-right corner, then click Profile (example@netwitness.com).
-
On the left side bar, click Email Notifications.
The Email Notifications page is displayed.
-
To enable a notification email, turn the toggle on ( ).
).
-
To disable a notification email, turn the toggle off ( )
)
Configure email notification preferences within the NetWitness Cloud Portal for the following event:
| Notification Type |
Description |
| Sensor Status |
This setting allows administrators to receive email notifications when the status of each sensor changes under the Sensor List tab. For example, if a sensor gets disconnected, you will receive an email notification. |
| Sensor Updates |
This setting allows administrators to receive email notifications for new sensor version updates, successful and failed sensor updates, and sensor release notes. |
| License Usage |
This setting allows administrators to receive email notifications when their data ingestion exceeds the daily limit based on the configured license. |
See also
Cloud Link Service Overview